The Top 8 Burp Suite Extensions That I Use to Hack Web Sites
When doing Web Application Penetration Tests, one tool dominates the desktops of most Security Consultants: Burp Suite Professional (https://portswigger.net). This comes as no surprise. It has solid performance, a ton of features, and most importantly, extensibility. Users can add features for nearly every type of web technology out there.
Here’s a short list of extensions, in no particular order, that we use on nearly every engagement in 2019.
- Flow
- Autorize
- Cloud Storage Tester
- RetireJS
- Active Scan++
- Upload Scanner
- JSON Web Tokens
- HTTP Request Smuggler
Flow
What it does
If you have used Burp Suite for any extended period of time, you will fall in love with being able to see everything that your browser is communicating to a web application. Trouble is, with some Burp Suite functions such as Scanner, Extender or Sequencer, the traffic is not visible within Burp Suite. Here is where you need Flow. It logs everything that Burp Suite sends. This comes in really handy when ensuring Scanner is still authenticated or ensuring Macros are working properly.
How to use it
Flow is easy to use, just install it and watch it proxy previously-hidden functions such as Active Scan.
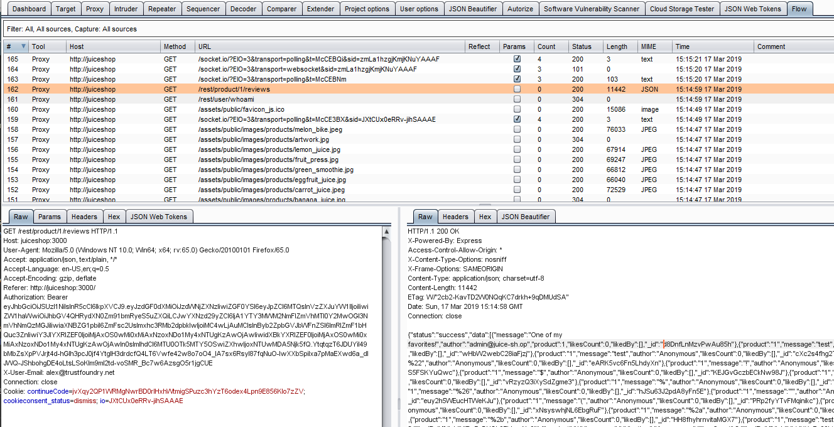
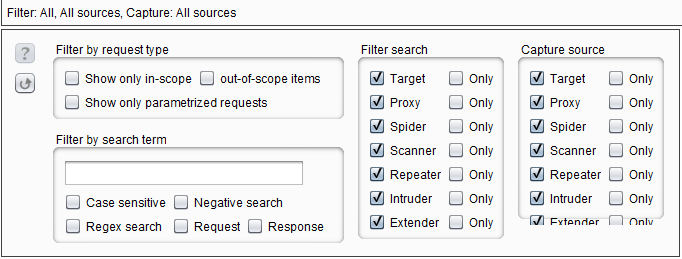
Customize what tools you see or don’t see by clicking the Filter bar at the top.
Pro tip
Move flow down to the bottom of all your extensions like so:
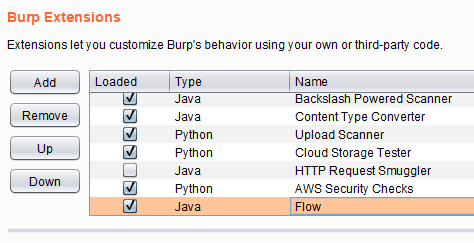
Extensions are used in the order they appear on that list and Flow may not log a particular extension if it is above that extension on the list.
Autorize
What it does
Testing for authorization issues on a site is tedious. In the past, testing involved:
- making a privileged function call
- sending that call to Repeater
- replacing privileged session tokens with a low-level user’s session tokens
- then re-sending the request to see if the low-level user can perform a privileged function
On an average site with 20-30 different administrative functions and a handful of different roles, this type of manual checking could take days. Thank goodness for Autorize. This plugin allows you to pop-in some session tokens and repeats each request it sees with those tokens.
How to use it
Log in as an unprivileged user and grab their session tokens. This can be a cookie or a header. Put those values in Autorize and it will replace then and resend each request it sees with those tokens.
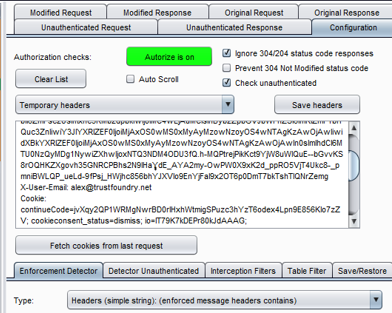
Now all you have to do is browse the site as an administrator and perform privileged functions. Autorize keeps a running list of privileged requests side-by-side with unprivileged ones so you can see at a glance if a low-level user can do things they should not be allowed to do.
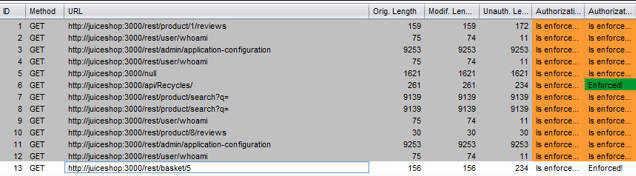
Pro tip
Paste the whole Authorization or cookie header into Autorize, including the “Authoriztion:” or “Cookie:” text.
Cloud Storage Tester
What it does
This extension can identify and test S3 buckets, as well as Google Storage buckets and Azure Storage containers, for common misconfiguration issues. With more and more sites utilizing cloud infrastructure, these types of misconfigurations become more and more important to watch out for.
How to use it
If you have the AWS Access Key and AWS Secret Key, then plug them in and click save. The extension will perform cloud storage tests while doing active scans using these keys. It is more likely that on an engagement, these keys will not be available. Without keys, Cloud Storage tester will still perform passive checks such as looking for public S3 buckets. The extension will add any issues it finds to the Target tab.
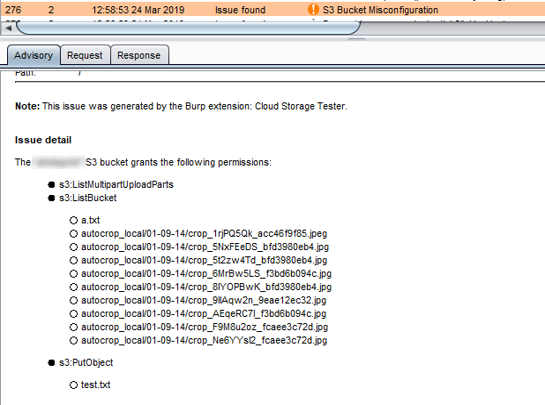
Verify AWS Access Key and AWS Secret Key using something like AWS CLI to ensure the tokens are working before using them in the Cloud Storage Tester extension.
RetireJS
What it does
RetireJS passively looks for out of date JavaScript libraries while you browse a site. Since the world is now obsessed with using JavaScript for everything, this type of extension is worth its weight in gold.
How to use it
Install the extension and browse/test the site as usual. Any out-of-date JavaScript libraries that are discovered will be flagged and included in Target tab with any other issues discovered.
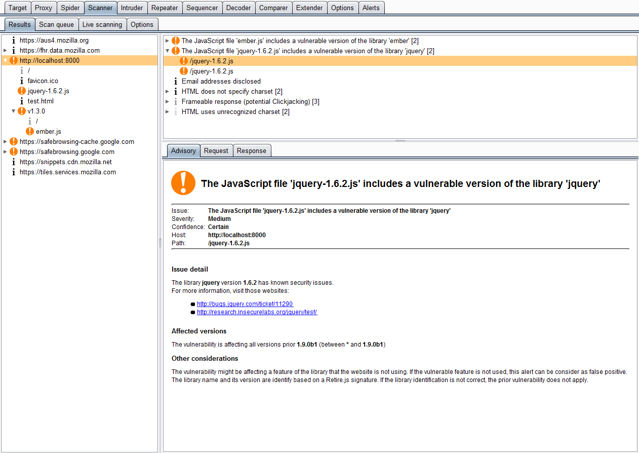
Pro tip
The extension links to known public vulnerabilities for the out-of-date libraries to give you hints on how to attack the application.
Active Scan++
What it does
ActiveScan++ extends Burp Suite’s active and passive scanning capabilities. Designed to add minimal network overhead, it identifies application behavior that may be of interest to advanced testers:
- Potential host header attacks (password reset poisoning, cache poisoning, DNS rebinding)
- Edge side includes
- XML input handling
- Suspicious input transformation (eg 7*7 => ’49’, \x41\x41 => ‘AA’)
- Passive-scanner issues that only occur during fuzzing (install the ‘Error Message Checks’ extension for maximum effectiveness)
It also adds checks for the following issues:
- Blind code injection via expression language, Ruby’s open() and Perl’s open()
- CVE-2014-6271/CVE-2014-6278 ‘shellshock’ and CVE-2015-2080, CVE-2017-5638, CVE-2017-12629, CVE-2018-11776
How to use it
Install the plugin and perform an Active Scan (Audit) of the web application. ActiveScan++ will perform the additional checks.
Pro tip
I used to avoid installing ActiveScan++ because it would never really find anything. But when a colleague of mine found Remote Code execution on a site using the extension, I was sold. This extension may not find things 98% of the time, but when it does, you will be glad you installed it.
Upload Scanner
What it does
We know that file upload functions are ripe for vulnerabilities. However, these vulnerabilities can sometimes be tricky to find. For example, if you upload a file and it is renamed and appears on another page, Burp Scanner will generally not know how to check these separate pages. This is where Upload Scanner comes in handy.
How to use it
Upload a file in the web application. In Burp Suite Proxy tab right click the upload request and select “Send to Upload Scanner”. There are so many options that another blog post is probably required, but the high-level workflow is like this:
- Start with the actual file upload request and response.
- Find the place where the file can be downloaded (ReDownloader request).
- Define start and ending markers in the original file upload response for pulling out values needed to make the ReDownloader request.
- Set up a ReDownloader request to use these values.
- Test all this out using “Send preflight request” and “Send ReDownloader request”.
- Click Start Scan to scan thousands of file upload tests.
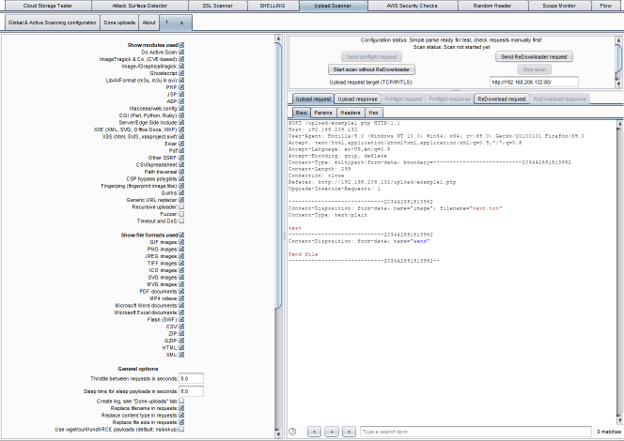
Pro tip
Watch file download requests and responses in Flow to make sure the scan is not encountering any errors.
JSON Web Tokens
What it does
JSON Web Tokens (JWT) are popping up everywhere. There are some common attacks that are easy enough to test for, but manually decoding and re-encoding the base64 values acan be tedious. This Extension makes it easy to decode and manipulate JSON web tokens (JWT) and automate common attacks.
How to use it
Send a request to Repeater and if there is a JWT in the request you will see a new tab like this:
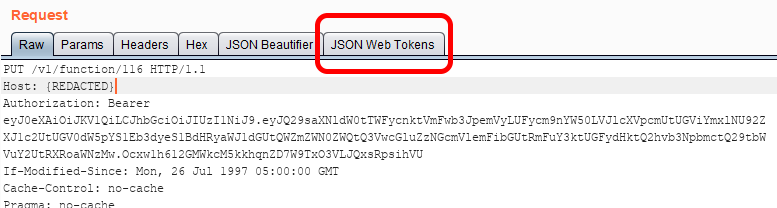
From this tab you can select any one of the common JWT attacks and re-send the request to see if it is successful.
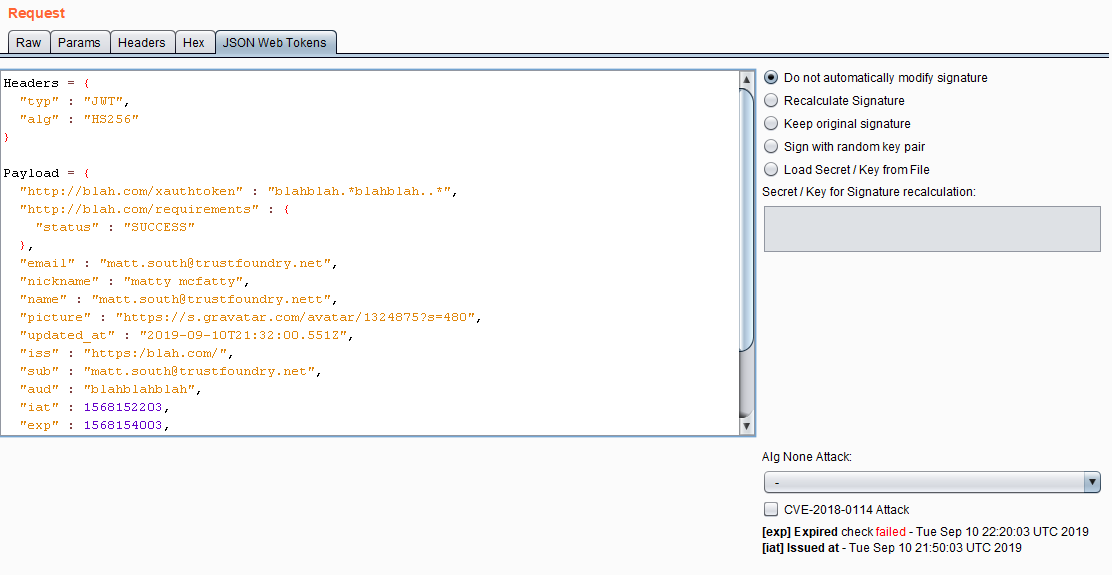
That tab will not appear if there is not a JWT in the request.
HTTP Request Smuggler
What it does
Request Smuggling is a newer class of vulnerabilities presented at BlackHat in 2019 by James Kettle (https://www.blackhat.com/us-19/briefings/schedule/index.html#http-desync-attacks-smashing-into-the-cell-next-door-15153). By tampering with Content-Length headers and Transfer-Encoding headers, you may be able to confuse load balancers, CDNs, WAFs or any number of HTTP proxies that sit in front of the actual web application server. This can lead to some interesting attack vectors as outlined in Kettle’s talk here: https://www.youtube.com/watch?v=-y82LadA7N4.
How to use it
This extension will automatically perform checks when doing Active Scanning on the web application and flag any suspicious behavior. Additionally, you can right-click an item in the Proxy History tab and select “Launch Smuggle Probe”. This could help determine if the application is vulnerable to TE-CL attacks or CL-TE attacks. Based on that, a Proof-of-Concept attack could be created manually.
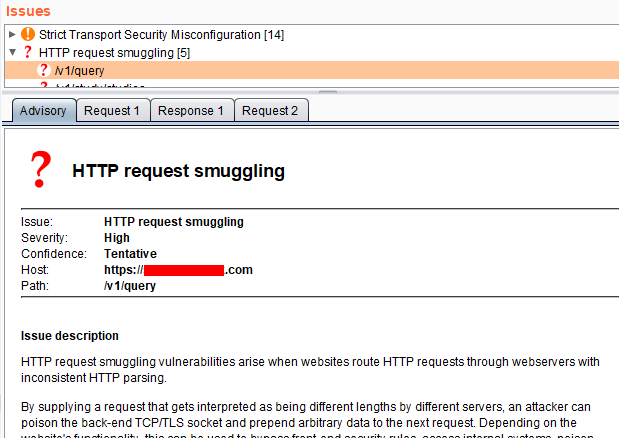
Pro tip
Do the labs over at Portswigger (https://portswigger.net/web-security/request-smuggling) to get a better idea of how to exploit these types of attacks.
Of course this is just a sample of the Burp extensions out there. When performing Web Application Penetration Testing, we always select Burp extensions based on the observed technology. Contact us for more information about our penetration testing methodology.
Is there an extension we missed? Let us know in the comments below.




Thank you , this is helping alot
Cant believe your didn’t mention the one that crafts a SQLmap command for you and launch it. I think that’s what it’s called. Very useful extension.
Sometimes we use CO2 for that, but we generally craft sqlmap manually and pass in the full request with -r.