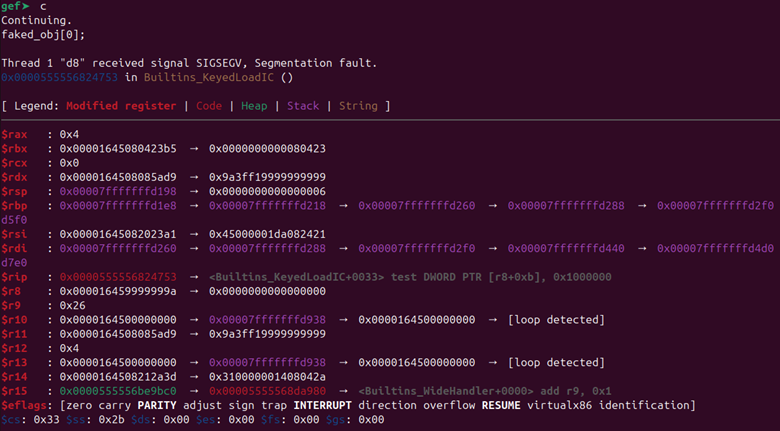
Our mission is to protect organizations from cyber threats, malicious attacks and hacking.
Penetration Testing for a More Secure World
TrustFoundry is a leading information security firm focused on penetration testing.
Breaking it for the better
The sophistication of malicious activity is relentlessly climbing as legitimate, mission-
critical applications and infrastructure grow in complexity.
Understand the potential risk within your technical infrastructure, and your compliance needs for critical applications.
TrustFoundry's full array of penetration testing services can help your business identify and eliminate security vulnerabilities.
Don't wait for a real attack, test your defenses and incident response safely with a team of experienced security experts.
Services we offer

Why trust us?
40
Years of Penetration
Testing Experience
1000+
Assessments
Delivered
100%
Customer
Satisfaction
100%+
100% Focused on
Penetration Testing
SUCCESS STORIES
What Our Clients Say
Out of the gate our experience with TrustFoundry was very positive. They did their own scoping research, and not having to coordinate our testing between sales and the testers saved valuable time. This is a highly experienced team that has proven themselves time and time again.

Travis, CISO
5 of 5 overall satisfactionWe wanted a vendor that had experience with Fortune 500 companies, and is quick to address our concerns and questions. In TrustFoundry we found a partner that was organized, had deep expertise, and was able to clearly explain everything that an organization from small to large would need.

Jug, CTO
5 of 5 overall satisfactionTrust Foundry is vital to our ongoing security and compliance efforts to protect our applications and networks. Their ability to simulate real-world attack scenarios and perform comprehensive testing helps to identify security weaknesses that other teams can miss.

David, VP of Information Security
5 of 5 overall satisfactionProfessional and knowledgeable team; great communication; reporting is awesome; always responsive; and really strong technical skills. I trust that they have conducted thorough pentests and feel confident in the results.

Andy, Director of Information Security
5 of 5 overall satisfactionTrustFoundry's communication top to bottom is hands down the best we've had from any partner we have used. This saved us a lot of frustration and time, but most importantly the results were exactly what we needed.

Elizabeth, Security Awareness Coordinator
5 of 5 overall satisfactionThe TrustFoundry team is extremely knowledgeable, professional, and responsive. The reports were well written and testing thorough. Weekly status updates and escalations of critical findings were also great.

Alev, Compliance Manger
5 of 5 overall satisfactionWe have worked with other pentesting firms that ran scans and outputted a report with little manual exploit effort, explanations or understanding. TrustFoundry walked us through their processes and was able to intelligently speak to the risk and impact for each finding.

Christy, Senior Information Security Engineer
5 of 5 overall satisfactionGreat communication, technical knowledge was awesome, integrated to our team seamlessly. We had a few different vendors who were not necessarily responsive, and did not have an in-depth penetration testing capability.

Scott, CTO
5 of 5 overall satisfactionThe quality of the work, findings, and reporting was phenomenal. The high level of communication and service really helped us stay on track and within our budget. We will be returning in the future as we develop our environment.

Alfredo, Director of Information Security
5 of 5 overall satisfactionTrustFoundry was a great team to work with. Quick to respond, happy to help and extremely flexible with us. Professionals through and through. We could not recommend them highly enough for application and network security.

Kyle, DevOps Engineer
5 of 5 overall satisfactionWe have engaged TrustFoundry to perform our annual pen testing in prior years with excellent results us years and have found the team to be very knowledgeable and customer focused at a very reasonable price point against other company offerings.

Michael, Information Security Manager
5 of 5 overall satisfactionWe had a great experience with TrustFoundry from scope of work all the way through remediation. The professionalism, communication, and detail in findings gave us a lot of confidence in the results. Price was great and responsiveness early on showed us we could return to in the future.

Kyle, Director of Engineering
5 of 5 overall satisfactionVery responsive and knowledgeable team. We have been working with TF and find that the service provided is best in class. Thank you TrustFoundry you will be hearing from me again!

Binu, CSO and Enterprise Architect
5 of 5 overall satisfactionJosiah, Alex, and Cody were incredibly easy to work with and we got a good result set from the engagement. Initial engagement was based on relationship between our organizations, however, we would absolutely choose TrustFoundry again based on the results and experience.

Jon
5 of 5 overall satisfactionThe team was easy to work with and provided a thorough test while being incredibly time efficient. What was scheduled to be a two week process, the team had our report ready within a week and was ready to provide a deep analysis.

Michael, Founder & CEO
5 of 5 overall satisfactionINDUSTRY INFORMATION
Security Insider
Filter